Monday 1 December 2008
The 3rd Gender: Engineering Student
Engineering students who already married or who is in a relationship (not with a dog or game title but with a human being) are excluded from this 3rd gender.
The commonality of engineering student is as follows.
1. There is no relationship in their lives, as there was , and there will be. No, No, No and forever
2. Instead, there are several ways of self-playing such as video game, facebook, blogging, Nintendo wii , text messaging, cartoon and so on. There is a rumor they created "dead on the bed" or "dead on the sofa" game, which means a person lies on the bed or sofa without doing anything including eating at all all day long, especially all weekends.
3. There are no marks on their calendars such as Lover's birthday, Christmas Eve, New year's Eve, Valentine's day
4. They hate couples, especially library couples. - Library couples are really annoying!! Get away and go somewhere...
5. They sometimes enjoy social dancing because this is the only allowed tim to hug or tough the other gender - Engineering students vs. Female, Engineering Students vs. Male, or sometimes Engineering students vs. Engineering students-
6. They like stalking, googling personal lives and peeping through face book.
7. They are lonely but they don't know how to express or resolve their feeling, even more, they don't want to admit their lonely feeling, they want to take this as part of their lives. Engineering students are lonely ....really...
8. They don't know how to spend their free time or holiday without work or computer.
9. They want a RELATIONSHIP. But they don;t know how to initiate. Therefore, it will not happen to them. Never and Ever.
10. Engineering students believe that they can make the world better than before by contributing creative engineering theory. (engineering: can be applied more than twice in a same manner) But the world would not be changed by engineering people but could be changed by business people. However, I am the one of them who believe engineers should contribute the world. (not world peace by Miss Universe, but fun/convenient world). Without this belief, engineer's life is only tragedy because we cannot make our partner happy!!
I found this works well in my territory, not only South Korea but also States, Pittsburgh.
I AM one of engineering student. Therefore, It will not happen to me, never and ever.
What a wonderful WORLD!!!
Wednesday 26 November 2008
PittStop rocked.
And I worked as one of the volunteers for PittStop Lindy Exchange workshop in Pittsburgh. It was amazing, amazing experience to meet swingers from outside Pittsburgh, they were from Ohio, York, DC, NewYork, Cleveland, Erie,Portland OR, Seattle WA, and many many cities.
I did lots of, lots of fun with them and made friends with them.
And now, I feel like I became a member of Pittsburgh community by working hardly with many volunteers. We worked from 1:00 pm to 6:00am and we olny slept for 4 or 5hours per day. I want to say thank you PittStop committe members - Lisa T, Linda gale, Lisa M, Bary, Anders, Joe, Dena, Laura, Jackery, David, Elizabath, Barbara and so on - They accepted and gave me an opportunity to work with , many rides to every locations and big hug. Like the song, I L-O-V-E Pittsburgh so much.
Thursday 6 November 2008
"a new dawn of American leadership."
If there is anyone out there who still doubts that America is a place where all things are possible, who still wonders if the dream of our founders is alive in our time, who still questions the power of our democracy, tonight is your answer.
It's the answer told by lines that stretched around schools and churches in numbers this nation has never seen, by people who waited three hours and four hours, many for the first time in their lives, because they believed that this time must be different, that their voices could be that difference.
It's the answer spoken by young and old, rich and poor, Democrat and Republican, black, white, Hispanic, Asian, Native American, gay, straight, disabled and not disabled. Americans who sent a message to the world that we have never been just a collection of individuals or a collection of red states and blue states.
We are, and always will be, the United States of America.
It's the answer that led those who've been told for so long by so many to be cynical and fearful and doubtful about what we can achieve to put their hands on the arc of history and bend it once more toward the hope of a better day.
It's been a long time coming, but tonight, because of what we did on this date in this election at this defining moment change has come to America.
A little bit earlier this evening, I received an extraordinarily gracious call from Senator McCain.Senator McCain fought long and hard in this campaign. And he's fought even longer and harder for the country that he loves. He has endured sacrifices for America that most of us cannot begin to imagine. We are better off for the service rendered by this brave and selfless leader.
I congratulate him; I congratulate Governor Palin for all that they've achieved. And I look forward to working with them to renew this nation's promise in the months ahead.
I want to thank my partner in this journey, a man who campaigned from his heart, and spoke for the men and women he grew up with on the streets of Scranton ... and rode with on the train home to Delaware, the vice president-elect of the United States, Joe Biden.
And I would not be standing here tonight without the unyielding support of my best friend for the last 16 years ... the rock of our family, the love of my life, the nation's next first lady ... Michelle Obama.Sasha and Malia ... I love you both more than you can imagine. And you have earned the new puppy that's coming with us ...to the new White House.
And while she's no longer with us, I know my grandmother's watching, along with the family that made me who I am. I miss them tonight. I know that my debt to them is beyond measure.To my sister Maya, my sister Alma, all my other brothers and sisters, thank you so much for all the support that you've given me. I am grateful to them.
And to my campaign manager, David Plouffe ... the unsung hero of this campaign, who built the best — the best political campaign, I think, in the history of the United States of America.To my chief strategist David Axelrod ... who's been a partner with me every step of the way.To the best campaign team ever assembled in the history of politics ... you made this happen, and I am forever grateful for what you've sacrificed to get it done.But above all, I will never forget who this victory truly belongs to. It belongs to you. It belongs to you.
I was never the likeliest candidate for this office. We didn't start with much money or many endorsements. Our campaign was not hatched in the halls of Washington. It began in the backyards of Des Moines and the living rooms of Concord and the front porches of Charleston. It was built by working men and women who dug into what little savings they had to give $5 and $10 and $20 to the cause.
It grew strength from the young people who rejected the myth of their generation's apathy ... who left their homes and their families for jobs that offered little pay and less sleep.It grew strength from the not-so-young people who braved the bitter cold and scorching heat to knock on doors of perfect strangers, and from the millions of Americans who volunteered and organized and proved that more than two centuries later a government of the people, by the people, and for the people has not perished from the Earth.
This is your victory.
And I know you didn't do this just to win an election. And I know you didn't do it for me.
You did it because you understand the enormity of the task that lies ahead. For even as we celebrate tonight, we know the challenges that tomorrow will bring are the greatest of our lifetime — two wars, a planet in peril, the worst financial crisis in a century.
Even as we stand here tonight, we know there are brave Americans waking up in the deserts of Iraq and the mountains of Afghanistan to risk their lives for us.
There are mothers and fathers who will lie awake after the children fall asleep and wonder how they'll make the mortgage or pay their doctors' bills or save enough for their child's college education.
There's new energy to harness, new jobs to be created, new schools to build, and threats to meet, alliances to repair.
The road ahead will be long. Our climb will be steep. We may not get there in one year or even in one term. But, America, I have never been more hopeful than I am tonight that we will get there.
I promise you, we as a people will get there.
AUDIENCE: Yes we can! Yes we can! Yes we can!
OBAMA: There will be setbacks and false starts. There are many who won't agree with every decision or policy I make as president. And we know the government can't solve every problem.
But I will always be honest with you about the challenges we face. I will listen to you, especially when we disagree. And, above all, I will ask you to join in the work of remaking this nation, the only way it's been done in America for 221 years — block by block, brick by brick, calloused hand by calloused hand.
What began 21 months ago in the depths of winter cannot end on this autumn night.
This victory alone is not the change we seek. It is only the chance for us to make that change. And that cannot happen if we go back to the way things were.
It can't happen without you, without a new spirit of service, a new spirit of sacrifice.
So let us summon a new spirit of patriotism, of responsibility, where each of us resolves to pitch in and work harder and look after not only ourselves but each other.
Let us remember that, if this financial crisis taught us anything, it's that we cannot have a thriving Wall Street while Main Street suffers.
In this country, we rise or fall as one nation, as one people. Let's resist the temptation to fall back on the same partisanship and pettiness and immaturity that has poisoned our politics for so long.
Let's remember that it was a man from this state who first carried the banner of the Republican Party to the White House, a party founded on the values of self-reliance and individual liberty and national unity.
Those are values that we all share. And while the Democratic Party has won a great victory tonight, we do so with a measure of humility and determination to heal the divides that have held back our progress.
As Lincoln said to a nation far more divided than ours, we are not enemies but friends. Though passion may have strained, it must not break our bonds of affection.
And to those Americans whose support I have yet to earn, I may not have won your vote tonight, but I hear your voices. I need your help. And I will be your president, too.
And to all those watching tonight from beyond our shores, from parliaments and palaces, to those who are huddled around radios in the forgotten corners of the world, our stories are singular, but our destiny is shared, and a new dawn of American leadership is at hand.
To those — to those who would tear the world down: We will defeat you. To those who seek peace and security: We support you. And to all those who have wondered if America's beacon still burns as bright: Tonight we proved once more that the true strength of our nation comes not from the might of our arms or the scale of our wealth, but from the enduring power of our ideals: democracy, liberty, opportunity and unyielding hope.
That's the true genius of America: that America can change. Our union can be perfected. What we've already achieved gives us hope for what we can and must achieve tomorrow.
This election had many firsts and many stories that will be told for generations. But one that's on my mind tonight's about a woman who cast her ballot in Atlanta. She's a lot like the millions of others who stood in line to make their voice heard in this election except for one thing: Ann Nixon Cooper is 106 years old.
She was born just a generation past slavery; a time when there were no cars on the road or planes in the sky; when someone like her couldn't vote for two reasons — because she was a woman and because of the color of her skin.
And tonight, I think about all that she's seen throughout her century in America — the heartache and the hope; the struggle and the progress; the times we were told that we can't, and the people who pressed on with that American creed: Yes we can.
At a time when women's voices were silenced and their hopes dismissed, she lived to see them stand up and speak out and reach for the ballot. Yes we can.
When there was despair in the dust bowl and depression across the land, she saw a nation conquer fear itself with a New Deal, new jobs, a new sense of common purpose. Yes we can.
AUDIENCE: Yes we can.
OBAMA: When the bombs fell on our harbor and tyranny threatened the world, she was there to witness a generation rise to greatness and a democracy was saved. Yes we can.
AUDIENCE: Yes we can.
OBAMA: She was there for the buses in Montgomery, the hoses in Birmingham, a bridge in Selma, and a preacher from Atlanta who told a people that We Shall Overcome. Yes we can.
AUDIENCE: Yes we can.
OBAMA: A man touched down on the moon, a wall came down in Berlin, a world was connected by our own science and imagination.
And this year, in this election, she touched her finger to a screen, and cast her vote, because after 106 years in America, through the best of times and the darkest of hours, she knows how America can change.Yes we can.AUDIENCE: Yes we can.
OBAMA: America, we have come so far. We have seen so much. But there is so much more to do. So tonight, let us ask ourselves — if our children should live to see the next century; if my daughters should be so lucky to live as long as Ann Nixon Cooper, what change will they see? What progress will we have made?
This is our chance to answer that call. This is our moment.
This is our time, to put our people back to work and open doors of opportunity for our kids; to restore prosperity and promote the cause of peace; to reclaim the American dream and reaffirm that fundamental truth, that, out of many, we are one; that while we breathe, we hope.
And where we are met with cynicism and doubts and those who tell us that we can't, we will respond with that timeless creed that sums up the spirit of a people: Yes, we can.
Thank you. God bless you. And may God bless the United States of America.God bless you, and may God bless the United States of America.
In the beginning of New America era
And I watched past Republican supporting states turned to blue.
At 11:00 pm, CNN announced "Barack Obama , Mr. president " and electoral vote results was 285 : 134. (now 338:162)
He is the first African-American president in United states and the only black senator in current government. He was just exposed to the media from 2004 President Candidate supporting speech expressing "One unity" for United States. And 3 years later, he was elected President candidate in Democratic party and finally became Mr.President one year after.
This is the memorable moment in the history, not only in the United States but also in the earth. He will be the symbolic president that no nation has ever had before - minority race, liberal politician, despite of lack of experience but beloved by young supporters/minority people/ ex-republican / rich and poor/ old and young/ Hispanic and white.
I am not a US citizen, and I am not a part of this historical moment, but I am deeply touched by this memorable moment and his speech - opportunity, unyielding hope, one united states, new spirit of responsibility and most of all his and Obama camp's "Yes, We CAN".
He gave the people "hope for change" and he succeeded to show the people a new American dream - anyone can be the president of united states, even though he is one of the African-American people, his father is not US citizen, his grand father and mother live in Kenya but American citizen supported him and elected him as Mr. President.
American people will remember that they were a part of this history forever , and I will remember I watched this memorable moment in Pittsburgh, PA.
Wednesday 15 October 2008
Swing Steps for Competition
Wednesday 8 October 2008
Balboa, Lindy, Jitterbug
Balboa is a smooth dance done in tightly closed couple position with subtle but striking footwork.
It's perfect for those fast numbers, and will fit well with both jitterbug and Lindy dancing.
It can be maniplated from the basic bal (balboa) to Bal-swing such as
basics, cross-overs, break-time, lollies, and throw-outs.
Lindy Hop
Lindy Hop is the original swing dance style from the 1930's and 1940's.
It's wildly popular in Europe and is the style of choice on the coasts: East Coast swing vs. West Coast swing.
This high energy style incorporates a distinctive, jazzy blend of footwork and kick variations.
Jitterbug
the basic 6 count footwork, several simple turns, fancy turns, smooth leads and hot moves of swing dance.
Tuesday 7 October 2008
Swing Lindy Workshop - Intermediate
Wednesday 1 October 2008
Swing , Latin, and Classic Dance
I started to learn swing dance since Sep. 2008 - currently I've learned Lindy, Balboa and east coast swing. Lindy is much more like Jive, especially foot work and 8 counts. But the difference between Latin and swing is the "dynamics". In Latin, the male and the female or ,what we call, the leader and the follower should have follow routine steps first and then both of them can manipulate just based on general routine steps. But in swing, the female, or the follower, can only follow the leader's movement whatever he choose. It's really dynamic and more fun!!!
I really , really like Swing and this is another happiness what I could enjoy in Pittsburgh.
Swing(Balboa) Lesson from Lisa
Swing (Lindy Hop) Lesson from Lisa
Saturday 27 September 2008
GUI tip
1) Subclass JFrame
a) Implement ActionListener
b) Private class implements ActionListener
c) Private static class implements ActionListener
d) Anonymous class implements ActionListener
Method2-Head first Java uses recipe 2b(J's favorite)
2) Don’t subclass anything
a) Implement ActionListener
b) Private class implements ActionListener
c) Private static class implements ActionListener
d) Anonymous class implements ActionListener
Saturday 20 September 2008
Swing City - Pittsburgh
Sunday 13 July 2008
"내 비밀은 이런 거야. 매우 간단한 거지. 오로지 마음으로 보아야만 정확하게 볼 수 있다는 거야. 가장 중요한 것은 눈에는 보이지 않는 법이야."
2.
"네 장미꽃을 그렇게 소중하게 만든 것은, 그 꽃을 위해 네가 소비한 시간이란다." "내가 나의 장미꽃을 위해 소비한 시간이라..." 잘 기억하기 위해 어린 왕자가 말했다
3.
" 그러나 네가 나를 기르고 길들이면 우린 서로 떨어질 수 없게 돼.넌 나에게 이 세상에서 단 하나뿐인 사람이 되고 난 너에게 둘도없는 친구가 될테니까."
4.
"나를 길들여줘...가령 오후 4시네 네가 온다면나는 3시부터 행복해지기 시작할거야...
그러나 만일,
네가 무턱대고 아무때나 찾아오면
난 언제부터 마음의 준비를 해야할지 모르니까..."
5.
"나는 해 지는 풍경이 좋아.우리 해지는 구경하러 가...""그렇지만 기다려야 해.""뭘 기다려?""해가 지길 기다려야 한단 말이야."
6.
사막은 아름다와. 사막이 아름다운건
어디엔가 우물이 숨어있기 때문이야. 눈으로는 찾을 수 없어, 마음으로 찾아야 해.
7.
"세상에서 가장 어려운일이 뭔지아니?"
"흠... 글쎄요. 돈버는일? 밥먹는일?"
"세상에서 가장 어려운일은 사람이 사람의 마음을 얻는일이란다.
각각의 얼굴만큼 다양한 각양각색의 마음을...
순간에도 수만가지의 생각이 떠오르는데
그 바람같은 마음이 머물게 한다는건 정말 어려운거란다."
8.
"지금은 슬프겠지만
그 슬픔이 가시고 나면(슬픔은 가시는 거니까) 넌 언제까지나 내 동무로 있을거고, 나와 함께 웃고 싶어 질꺼야."
9.
"사람들은 이 진리를 잊어버렸어."
여우가 말했다. "하지만 넌 그것을 잊어서는 안돼. 넌 네가 길들인 것에 대해 언제까지나 책임을 지어야 하는 거야. 넌 네 장미에 대해 책임이 있어..."
"난 나의 장미에 대해 책임이 있어." 잘 기억하기 위해 어린 왕자가 되뇌었다.
10.
다른 사람에게는 결코 열어주지 않는 문을...
당신에게만 열어주는 사람이 있다면
그 사람이야 말로... 당신의 진정한 친구이다.
Wednesday 4 June 2008
김진명의 킹 메이커
2007 07/17 뉴스메이커 733호
이른 아침부터 굵은 장대비가 억수같이 내리꽂던 7월 4일. 소설가 김진명(50)을 만나기 위해 길을 나섰다. 그의 신작 ‘킹메이커’가 논란을 불러일으키고 있기 때문이다. ‘킹메이커’는 노무현 대통령이 친미 성향의 이명박을 대통령으로 만들려는 미국 CIA의 공작에 맞서 현재 미국연방구치소에 수감된 김경준을 연말 대선 직전 국내로 송환하려는 시도를 다루고 있다. 김경준은 이명박 후보의 연루의혹이 제기된 옵셔널벤처스코리아(BBK투자자문 후신) 주가조작사건의 주범이다. 이 소설이 범상치 않은 이유는 대선주자들의 실명을 거론하며 소문으로 돌고 있는 그들을 둘러싼 무성한 흉허물을 직접적으로 들먹이고 있기 때문이다. 뿐만 아니라 작가 자신은 2004년 미국 대통령 선거에서 부시가 당선되는 데 결정적 기여를 했다고 책 서두에서 주장하고 있다. 김진명은 “당시 케리에게 약 6%를 리드당하고 있던 부시에게 내가 북한 핵과 관련해 모종의 제안을 했고 부시는 즉각 승낙의 신호를 보내옴으로써 선거에서 이길 수 있었다”고 밝혔다(소설 속에서는 ‘킹메이커’로 등장하는 인물 앨런 차가 작가 자신을 투영한 것이라고 했다). 장대비를 뚫고 김진명이 있는 충북 제천까지 내려가는 동안 혼란스러웠던 이유다. 의구심은 3시간 가까이 진행한 인터뷰를 끝내고 서울로 돌아오는 길에도 사라지지 않았다. 그러나 김진명은 인터뷰 중 거듭 “I’m Sure”라며 자신의 말이 진실임을 확언했다. 그는 소설 ‘킹메이커’를 불과 보름 만에 완성했다고 말했다. - 책 서두에, 2004년 6월 부시에게 북한 핵을 평화적으로 해결할 수 있는 이미지를 부여하면 케리에게 뒤지고 있던 그가 역전할 것으로 보고 모종의 제안을 했고 그게 받아들여졌다고 주장했다. 어떤 선을 통해 부시에게 제안했다는 것인가.“아직 살아 있는 루트(경로)이기 때문에 공개하기 어렵다. 부시는 6월 25일 당시 미국 국무장관이었던 콜린 파월에게 ‘이념과 체제가 다르지만 우리는 북한과 세계평화를 위해 협조할 용의가 있다’는 성명을 발표하게 했다. 또 같은 날 안보보좌관 곤돌리사 라이스가 특별기 편으로 한국에 왔다. 곤돌리사는 당시 다른 나라를 들르지 않고 한국만 왔는데 특별한 방한 이유가 없었다. 그저 몇 시간 동안 한국에 머물다 간 게 다였다. 이게 내가 보낸 제안에 부시가 보내온 신호다. 당시 부시는 독선적이고 오만한 이미지 때문에 케리에게 뒤져 있었다. 또 이라크전쟁 후 전투기를 괌의 엔더슨 기지로 옮겨 평양을 폭격하는 훈련을 했다. 때문에 부시가 다른 전쟁, 즉 북한 침략을 준비하는 것이 아니냐는 우려가 국내외적으로 컸다. 난 부시가 북한 핵문제를 총 한 방 안 쓰고, 피 한 방울 안 흘리고 해결한다면 선거에서 온건한 이미지를 회복해 당선될 것이라 확신했다. 당시 난 미국이 북한에 온건한 메시지를 전하면 북한 김정일도 대량살상무기와 관련해 미국과 대화할 수 있다는 메시지를 발표하게 할 수 있다고 했다. 하지만 김정일을 접촉하는 데 실패해 절반의 성공만 거둔 셈이다.”- 왜 실패했나.“처음엔 외교문제에 관한한 김정일의 오른팔인 한성렬 북한 유엔대표부 부대사(현재 북한 군축평화연구소 대리소장)를 통해 김정일을 움직이려고 했다. 한 부대사에게 지금 당신이 여기에 있을 때가 아니지 않느냐며 빨리 평양에 가라고 주문했다. 하지만 그는 일이 잘못되면 숙청당할까봐 하지 않았다. 난 박근혜 당시 한나라당 대표를 찾아갔다. 그가 2002년 평양을 방문했을 때 김정일과 특이한 스킨십(공식적인 딱딱한 분위기가 아닌 화기애애한 의미로 말함)을 이루었다고 봤기 때문이다. 마침 박근혜도 곤돌리사 라이스의 돌발적 방한과 콜린 파월의 비상한 성명 발표를 매우 이상하게 생각했다고 말했다. 난 비서실장을 물러가게 하고 그 내막을 이야기했다. 그리고 평양에 올라가서 김정일을 설득하라고 권유했다. 김정일에게 ‘오빠’라 부르며 미국과 핵무기에 대해 진지하게 대화할 용의가 있다고 발표하게 만들라고 주문했다. 그러면 한반도가 미국 대통령을 뽑는 것이 되고 한반도의 도움으로 대통령에 당선된 인물은 임기 내내 한반도를 위해 많은 일을 할 것이라고 설득했다. 하지만 박근혜는 당시 한나라당 대표라는 자리에 대한 부담감 때문인지 결국 평양에 가지 않았다.”- 이 소설의 주요 인물 중 하나는 케이준으로 명명된 김경준이다. 김경준의 한국 송환이 늦어지고 있는 이유가 미국 CIA의 음모 때문이라고 믿는 것인가.“미국은 반미성향의 노무현이 정권을 잡으면서 힘들었기 때문에 이번엔 친미대통령이 되기를 바란다. CIA는 한발 더 나아가는데 거기에 걸린 게 김경준이다. 김경준은 송환재판을 두 번 받았고 그때마다 한국 송환이 판결됐다. 그런데 재산과 관련된 재판에서는 한 판사로부터 이해할 수 없는 판결이 나왔다. 김경준이 한국에서 훔쳐간 돈이 적법하다는 것이다. 그래서 김경준이 3년여간 한국에 못 온 것이다. CIA가 개입하지 않았다면 있을 수 없는 일이다. 만약 이명박이 대통령에 뽑히면 미국은 한국 대통령의 약점을 잡고 있는 셈이니 국내 정치에 더 개입할 수 있다.”- 소설에는 김경준의 누나인 에리카 김과 이명박의 염문설이 나온다. 명예훼손으로 고소고발당할 수도 있을 것 같은데. “이명박과 에리카 김의 스캔들은 5~6년 전부터 LA 교민사회에 파다했다. 이명박이 무엇에 홀리지 않은 한 왜 한국에 뿌리도 없는 30대 초반의 김경준에게 수백억의 돈을 투자했다고 생각하나. 에리카김과 이명박은 미국에서 만나 어울렸고, 에리카 김이 명문대를 졸업한 자기 동생이 있으니 이명박에게 잘 돌봐달라고 한 것이다. 그렇지 않고서야 달리 설명할 방법이 없다. 난 2005년과 2006년 LA에 가서 이를 직접 취재했다. 이명박과 에리카김의 스캔들에 대해 언론이 제기하지 못하니까 작가인 내가 한 것이다. 내 이야기가 잘못 됐으면 날 명예훼손으로 고소하라고 하라.”- 박근혜와 최태민 목사가 그렇고 그런 사이이며 둘 사이에 숨겨놓은 애까지 있다는 소문까지 책에서 거론했다.
“박근혜와 최태민 목사 사이의 아이 이야기는 내가 지어낸 것이다. 때문에 난 박근혜가 명예훼손으로 내게 소송을 거는 게 옳다고 생각한다. 내가 이 책을 쓴 목적은 개개인의 약점을 드러내고자 한 게 아니다. 2004년처럼 의혹이나 악소문 때문에 선거가 좌우되지 않기를 바라는 마음에서다. 의혹이나 흑색선전에 대처하는 사회적 검증문화를 정립하는 게 무엇보다 중요하다. 그런 면에서 이명박이 ‘소이부답(笑而不答, 웃기만 하고 대답하지 않는다)’이라고 말한 것은 말도 안 된다. 어쩌면 그 말에 화가 나 소설을 쓴 건지도 모른다. 박근혜의 경우는 그가 모든 검증을 받아들이겠다고 했으니, 내가 최고의 악소문을 만들어낸 것이다. 그가 어떻게 받아들이는지 보고 싶었고, 그가 소문의 진상을 당당히 밝히면 난 그에게 공개 사과할 것이다.”- 정치권의 반응은 없나.“없다. 왜냐하면 반응을 보이는 즉시 추락이기 때문이다. 그들과 관련된 내용은 팩트(사실)이기 때문이다. 그들이 숨기고 싶은 것을 내가 이야기한 것이다.”- 전작 ‘나비야 청산 가자’도 그렇고 이번 소설도 손학규를 지지하는 것처럼 비친다. 김대중 전대통령의 발언형식을 빌어 대선 주자 중 유일하게 손학규를 긍정적으로 묘사했다. “선거는 국민의 책임이 크다. 국민의 역량만큼 지도자를 뽑는 것이기 때문이다. 후진국은 고무신과 막걸리에 선거판이 갈리고 선진국은 누가 더 역량 있는지를 가늠해 인재를 뽑는다. 우리나라 국민의 투표수준은 낮다. 정치풍토를 모르기 때문이다. 한 사람이 보통 사람으로 출발해 대통령이 되기까지 어떤 과정을 거치는지 몰라 괜찮은 사람을 뽑지 못한다. 선전이나 힘에 좌우돼 제대로 판을 읽지 못한다. 이명박은 어떤 면에서는 대통령이 되기 힘든 사람인데 지지율이 높다는 게 이를 입증하는 것이다. 이런 정치풍토에서 손학규라는 사람이 대선 후보 반열에 올랐다는 것은 기적과 같은 일이다. 이명박은 많은 돈과 명성으로, 박근혜는 경북 대구의 절대적 지지로, 정동영은 그 뒤에 김대중이 있다. 하지만 손학규는 그런 후광이 없다. 10여 년간 정치를 하고도 2억 몇천짜리 아파트 한 채가 재산의 전부다. 그걸 북돋울 필요가 있다. 언론은 강자 편이어서 이를 드러내지 않기 때문에 작가인 나라도 거론하는 것이다. 결코 손학규를 지지해서가 아니다.”- 손학규 후보와 친분이 있나.“국내정치 특히 선거를 이대로 두면 안 되겠다 생각할 때 국내 정치인을 두루 만나본 적이 있다. 2005년과 2006년의 일이다. 그때 이명박, 고건, 손학규 등 대다수의 후보를 만났다. 그때 한 번 만난 게 전부다.”- 손학규가 범여권의 대선후보로 낙점될 것으로 보나.“난 ‘나비야 청산가자’를 쓸 때 이미 손학규가 여권으로 갈 줄 알았다. 정치가 뭐고 힘이 뭔지 아는 사람은 보인다. 손학규가 범여권의 후보가 되는 것은 당연하다. 김대중은 선거의 귀재다. 노무현을 당선시킨 것도 그다. 이번 선거도 김대중이 쥐락펴락할 것이다. 이번 대선의 본질은 반노무현이다. 노무현 하면 사람들이 두드러기를 일으켜 한나라당 지지율이 높은 것이다. 그런데 정동영, 김근태, 김혁규, 이해찬은 모두 노무현과 살을 섞은 사람들 아니냐. 객관적으로 보면 손학규가 범여로 넘어가지 않으면 선거가 안 되는 것이다. 누구보다 김대중이 이를 잘 알고 있다. 손학규가 가장 어려움을 겪던 시기에 북한과의 자리를 만들어준 게 김대중이다. 김대중은 당시 ‘북한에서는 손학규를 참 좋아한다’고 말했다. 손학규가 범여로 갔기 때문에 흥행이 되는 것이고 만약 여권 후보들이 손학규를 이용만 한다면 결국 선거를 망치는 일이 될 것이다.”- 이번 선거의 전망을 어떻게 보나.“이명박이 한나라당 경선에서 박근혜를 이기지 못할 것으로 본다. 우리나라 국민은 지도자에 대해 윤리의식이 강하다. 한두 건도 아니고 이명박은 살아온 인생 자체가 지도자와 거리가 멀다. 최소한 노무현 정도는 돼야지 이명박이 대통령이 되면 나라가 안 선다. 난 박근혜와 손학규의 싸움이 될 것으로 본다. 두 사람 중 누가 되면 좋겠다는 마음은 아직 정하지 않았다.”- 소설을 통해 2008년 미국 대통령 선거에 북한의 플루토늄 20㎏을 활용해야 한다고 주장했다. 또 직접 나서겠다는 것인가. “북한의 플루토늄 20㎏만 활용하면 한반도가 미국 대통령을 선택할 수 있는데 누구도 나서지 않고 있으니 갑갑하다. 북한은 지금 어쩔 수 없이 핵포기의 수순을 밟고 있다. 원자로를 폐쇄하고 나면 이미 확보한 플루토늄 20㎏을 어떻게 하느냐의 문제가 대두된다. 이때 우리가 공화당 후보든 민주당 후보든 한 사람을 평양으로 불러 김정일이 직접 그의 팔에 안겨주게 하거나 그가 미국으로 가져가거나 남한의 기술자를 불러 북한에서 해체하는 것을 감독하고 떠나거나 하게 하면 그는 미국 대통령에 당선될 것이다. 미국이 골머리를 앓는 가장 큰 외교문제는 북한 핵문제이기 때문이다. 그럼 한반도가 미국 대통령을 뽑게 되는 것이고 한반도의 도움을 얻은 미국 대통령은 8년의 임기 동안 한반도를 위해 엄청난 노력을 기울일 것이다. 이번 대선에서 누가 대통령이 되든 나는 이 문제를 종용할 것이다. 하지만 정부가 나서지 않는다면 내가 또 움직일 것이다.” <글·박주연 기자 jypark@kyunghyang.com><사진·김세구 기자 k39@kyunghyang.com>
Monday 5 May 2008
Paper Submission
Coolest Professor in CMU
I enjoyed his two classes a lot, received great comments from final project. Everytime I feel lots of energies and enormous enthusiasm from him. He is a really really cool professor in CMU.
Pittsburgh Symphony Orchestra
Monday 28 April 2008
The general structure of a writing piece
- Introduction
- what are you taling of ?
- What are you taiking about it?
- Why now?
- so what?
- conclusion
Wednesday 16 April 2008
Lessons from Steve Jobs
“Your time is limited, so don’t waste it living someone else’s life. Don’t be trapped by dogma - which is living with the results of other people’s thinking. Don’t let the noise of other’s opinions drown out your own inner voice. And most important, have the courage to follow your heart and intuition. They somehow already know what you truly want to become. Everything else is secondary.”
“You know, we don’t grow most of the food we eat. We wear clothes other people make. We speak a language that other people developed. We use a mathematics that other people evolved… I mean, we’re constantly taking things. It’s a wonderful, ecstatic feeling to create something that puts it back in the pool of human experience and knowledge.”
“We’re here to put a dent in the universe. Otherwise why else even be here?”
“I’m the only person I know that’s lost a quarter of a billion dollars in one year…. It’s very character-building.”
“I would trade all of my technology for an afternoon with Socrates.”
“There’s a phrase in Buddhism, ‘Beginner’s mind.’ It’s wonderful to have a beginner’s mind.”
“Innovation distinguishes between a leader and a follower.”
“We think basically you watch television to turn your brain off, and you work on your computer when you want to turn your brain on.”
“Be a yardstick of quality. Some people aren’t used to an environment where excellence is expected.”
Thursday 10 April 2008
China or India
First, China leads India in terms of economy growth rate; therefore, we can expect much more return on investments than India. China's GDP totaled 3,100 billion U.S. dollars in the year of 2007, up to 11 percent over the same period last year, according to the China National Bank. However, India raised GDP growth of 8.7 percent, up to 928billion dollars in total GDP according to the Reserve Bank of India. This economic data appears to be sustainable until two or three years after, as we have seen so far.
Second, China leads India in terms of market size; therefore, we can expect much more opportunities than India. China’s GDP per person was 2,280 dollars in the year of 2007; on the other hand, India’s GDP per person was 830 dollars in the same year according to National Bank. As the China’s economy grows, the brand market will grows as well. This means that international brand market will grows much more rapidly in China than in India. In addition, because China is the site for the next Olympic Games, all the global companies will invest or try to enter this attractive market by the year of 2010.
Third, China’s dominant industry is manufacturing; however, India is strong in technology and IT services high value industry, but is obviously not a high volume industry. Typically, service industry does not rely on high, intensive capital, on which China’s manufacturing industry has relied to a great extent. By this reason, a large number of foreign investments are turning toward China, and we need to move forward with the same reason.
In conclusion, in terms of growth rate, market size, and the event of Beijing Olympic, to invest China is the best choice. The decision of China investment is most critical to the growth of our company and the right decision will lead us to be a global leader.
Tuesday 8 April 2008
How to prepare Good meeting
1. Purpose
- critical issues
2. Agenda
- 1page
- grouping topics
- prioritize topics
- Keep track on time (time keeper) + notes (Note taker)
- Responsibilities
3. People
- pick right participants
4. Place + Time
- Bad Time: lunch, at 5:00PM, Friday afternoon, Monday early morning
- Best Time: Tuesday/Wednesday/Thursday morning
- don't bring high sugar stuff, pasta, pizza
- Place: adequate size, depends on group size, visual aids
- Time: don't over 2 hours
5. Invite /DRAFT Agenda
- please review, comment about attached draft agenda
6. Resend with changes/ P
- based on all sets, well-prepared to the meeting
7. Arrive Early
- host should arrive early.
8. Start on Time
9. Set the Tone
10. Run the meeting
11. Meeting Minustes/Meeting Summary
12. Actions
Monday 7 April 2008
7 things employee want most to be happy at work
1. Appreciation
2. Respect
3. Trust
4. Individual growth
5. A good boss
6. Compatible co-workers
7. A sense of purpose
By Marlilyn Gardner
Thursday 3 April 2008
Interview Tip
2) Resume : Right Upfront by two hands
3) Interrupted behavior/ Eye Contact
4) Asset Points (Weaving asset points)
5) Memorable Story/ Differentiation
6) Company Knowledge
7) Enthusiasm/ Potential / Simple/ Engage / Enjoy
8) Action Statement - I created/developed/improved ....
9) Result Oriented/ Add Quatative number
10) How handle difficult question/situation
11) Ask Good Question ; Poze/ Scilence/ At the end
12) Specific Story about team skill (worst team experience )
13) Hardworking
14) Handle salary question, elogance
15) Ask Next step; Ask email address
16) Last chabge; Ending(Handshake), Ask Next Step
Monday 28 January 2008
Steve Job's Presentation Tip
2. Demonstrate enthusiasm.
3. Provide an outline.
4. Make numbers meaningful.
5. Try for an unforgettable moment.
6. Create visual slides.
7. Give 'em a show.
8. Don't sweat the small stuff.
9. Sell the benefit.
10. Rehearse, rehearse, rehearse.
Wednesday 23 January 2008
When to use Passive
2) when your readers don't care who did the action
3) when you don't want the readers to know who did the action
4) when the receiver of action is more important than the doer of the action
5) when you wish to be less confrontational
Goal with SMART
There are famous tool to make good goal.
SMART
Specific, Measurable, Attainable, Relevant, Time-Bound
Monday 21 January 2008
SOA
Architecture view: a set of architectural principles, patterns and criteria which address characteristics such as modularity, encapsulation, loose coupling, separation of concerns, reuse, composability and single implementation
Implementation View: a programming model complete with standards, tools and technologies such as Web Services
An SOA is composed of multiple layers. At the heart of the SOA is the Service Model that defines Services and Components that realize them
Service modeling – what we model
Layer 1 which is the bottom layer describes operational systems. This layer contains existing systems or applications including existing CRM and ERP packaged applications, legacy applications and “older” object-oriented system implementations as well as business intelligence applications. The composite layered architecture of an SOA can leverage existing systems, integrate them using service-oriented integration.
Layer 2 is the component layer which used container–based technologies and designs used in typical component-based development.
Layer 3 provides for the mechanism to take enterprise scale components, business unit specific components and in some cases project specific components and provides services through their interfaces. The interfaces get exported out as service descriptions in this layer, where services exist in isolation or as composite services.
Level 4 is an evolution of service composition into flows or choreographies of services bundled into a flow to act as an application. These applications support specific use-cases and business processes. Here, visual flow composition tools such as WebSphere WBI-Modeler can be used for design of application flow.
Layer 5, the presentation layer is usually out of scope for an SOA. However, it is depicted because some recent standards such as Web Services for remote Portlets version 2.0 may indeed leverage Web Services at the application interface or presentation level. It is also important to note that SOA decouples the user interface from the components.
Layer 6 enables the integration of services through the introduction of a reliable and intelligent routing, protocol mediation, and other transformation mechanisms often described as the Enterprise Service Bus .
Layer7 ensures quality of service through sense-and–respond mechanisms and tools that monitor the health of SOA applications, including the all important standards implementations of WS-Management.
Wednesday 16 January 2008
Human Computation and Louis von Ahn
Luis von Ahn, he is a really, really, really genius!!!
I studied MPEG1,2 4 and MPEG7 10 years ago.
But still how to abstract specific objects from image and how to describe the relevant objects are open problem in image processing area.
But he solved this by "human computation" concept.
His main idea is like this;
let people compute for opem problem which computer cannot solved yet.
But use the people with fun and for free!
He is one of the Cooooooolest guy , a professor of CMU , as I ever met.....
(I'm going to have his class in this semester!!!!)
His PhD thesis was CAPTCHA (A program that can tell whether it suers is a human or a computer) in 2005.
a program that can generate and grade test that:
A.most humans can pass
B.current computer programs cannot pass
The official CAPTCHA site : http://www.captcha.net/
http://recaptcha.net/
Human Computation : http://www.cs.cmu.edu/~biglou/research.html
Luis von Ahn:http://www.cs.cmu.edu/~biglou/
Tuesday 15 January 2008
Simplicity and Separation of Concern
"Insecure managers create complexity. Frightened, nervous managers use think, convoluted planning books and busy slides filled with everything they've known since childhood. Real leaders don't need clutter. People mush have the self-confidence to be clear, precise, to be sure that every person in their organization - highest to lowest - understands what the business is trying to achieve. But it is not easy.You cannot believe how hard it is for people to be simple, how much they fear being simple. They worry that if they are simple, people will think they are simple minded. In reality, of course, it is just the reverse. Clear, tough-minded people are the most simple." by Jack Welch.
I 100% agreed about Jack Welch's last expression; "Clear minded people are the most simple".
Software architect is one of very hard occupation in the world, I think.

There are too many constraints in the company and technology and too many uncertainties in the business policy. However, software architect should make architectural decision and meet many different business objectives. And architectural decision should be reasonable, objective, and meet stake holder's totally different views; CEO wants numbers, CTO wants reliability, developers want codes, designers want lots of diagrams.....Although this complex and different perspectives, software architect make "simple" architectural decision. Simple architecture is the key for architectural decision. I paraded Yoda's saying in the movie "Star Wars", "May the force be with you."; My favorites :-) !!!
Monday 14 January 2008
Foundation Facility
Java Messaging service offers a unified wrapper over queuing mechanisms. The framework wraps the JMS implementation and provides methods for applications to use this service without knowledge of the underlying queuing mechanism or the JMS API. The JMS API offers a asynchronous send and receive mechanisms and also a synchronous send and receive mechanism for application clients. The synchronous implementation is a convenience implementation which calls the send and then the receive methods with an appropriate timeout. The mechanism uses the JMS correlation id to associate the request and the response. The framework also implements a wrapper over a JMS Topic thereby allowing an application to work in a publish subscribe mode.
Logging
This supports for reporting application events into persistent storage areas. Logging provides precise context about a run of the application. Once inserted into the code, the generation of logging output requires no human intervention. Second, log output can be saved in a persistent medium to be studied at a later time.
Rules
It provide flexibility to application design and development by externalizing dynamic business logic. As some areas of the business are more susceptible to change than others. It is important to therefore have a mechanism that allows an application to identify areas that are likely to change and externalize the logic contained within them. This changes should be managed is a such a manner that there is no to less development effort required. It uses code generator to generate rule classes. Rule classes run in the same address space as the application program. This enhances performance as rule classes run in the same address space and use the same thread of execution, they share the transaction database session context for data. This avoids reads from database for data that is already loaded. Rules can also be dynamically changed by integrating with dynamic class loader.
Dynamic class loading:
This facilitates deployment of business rules dynamically without stopping the application server. Rules as mentioned above are business logic that changes frequently and needs to be deployed on the application server without restarting the application server. Rules are deployed as jar files in the application server, any changes to the rules would negotiate a re-deployment of the jar files. Currently it is not recommended that the hot deployment option of the application server be used. This is because the application server vendors claim that it might cause potential synchronization problems with the deployed application and might cause deployed applications to be deleted or modified incorrectly.Custom class loader load classes directly from the disk. It scans a pre-defined area on the file system for changed files based on time stamp. Clients already in middle of a method call will continue to use the old class, while new clients will receive an object from the changed class. It checks for modified classes on configurable time based interval.
Configuration:
It supports for retrieving of application parameters defined in properties file. It synchronizes with the changes made to the application parameters while the application is running. This component uses caching and logging architectural mechanisms. Configuration allows for providing set of properties in a different properties file to
Helpers
The Framework offers various helper functions to facilitate the building of framework components. These components are expected to be re-used across various other sophisticated framework facilities or components.The following helpers are available as part of the framework. These facilities are implemented as helpers as any improvements to these facilities can be done in a central place benefiting all framework components that use them. For example, if there are changes to reflection helper to leverage performance enhancements to the next version of J2SE, then all components will benefit from the same. Similarly the XML Helper wraps the DOM implementation of Xerxes and provides an easy to use interface. The XML Helper includes some significant performance enhancements in the way commonly used XPath (/Customer/Name/) expressions are evaluated. It uses a custom mechanism for these kind of expressions instead of the much slower XPath API. XPath API is still supported for the complete XPath specification.
Error and Exception Mechanism:
This architectural mechanism handles application errors and loggs them as per standard strategy. Error handling supports for multi-lingual error messages for the same error codes. Two named exceptions viz FrameworkException and BusinessException are provided to be used to denote any application errors. Unique error code is assigned with each exception to identify the error.
Service locator
This is a deviation of the standard service locator pattern. It provides transparent object access to applications or other framework components. The service locator abstracts the service discovery process. This discovers a service based on a set of configuration parameters provided. This will then return an object of the service based on the parameter defined. The service locator handles the discovery of JNDI services apart from specific services like EJBs, JMS handles and POJOs. It caches JNDI resources to avoid lookups for each invocation.
Alert
This architectural service provides mechanism for sending alerts for an event. Events needs to be registered with alert service. Event handlers are implemented that handles the event. Support for alerting by SMS and Email is provided using SMS and Mail helper architectural components. Events have information as required by it’s event handler. Client provides those information in the Event and does not need to know about the recipients and mode of alerts. Event handler identifies the list of recipients and modes of sending alert. Alerts are sent asynchronously where client does not wait until alert is sent.
Reporting for batches
This architectural service is a wrapper over third party, OZ reporting, tool and provides option to plug-in another reporting tool in future without change in the client code. OLTP reports will continue in the same style as the existing KB system. Mainly this service is used by batch. Report service supports two modes of execution, synchronous and asynchronous. In asynchronous execution mode, the client request a report and then poll for the status based on the report task ID that was provided when requesting a report. In synchronous execution mode, the client waits for the completion of the report.
Mail component provides facility to send an email. Mail shields client from internals of sending email. Client is not required to know about the details on how to send mails. Mail component currently is used by Alert. Mail component currently inserts a record in a table owned by e-business team. E-business team finally reads records from the table and sends mail using their existing mail gateway.
SMS
SMS component provides facility to send a SMS. SMS shields client from internals of sending SMS. Client is not required to know about the details on how to send SMS. SMS component currently is used by Alert. SMS component currently inserts a record in a table owned by e-business team. E-business team finally reads records from the table and sends SMS using their existing SMS gateway.
Data Compression
Data compression implements a simplified API over the GZIP implementation. This mechanism can be used to compress data being transferred from the channel tier to the application tier or from the client to the channel tier. This mechanism can be used where-in the available bandwidth mandates a data compression mechanism. By implementing a standard compression algorithm, the data compression mechanism allows even third-party applications to compress data.
Charset Conversion
This supports for conversion from EBCDIC character set to ASCII character set and vice versa. Client code need not code for character conversion every time instead they can use this component.
FTP helper
FTP helper assists in listing and exchanging files between two servers. This uses the Apache commons FTP library, but makes modifications to the open-source library by providing support for the IBM mainframe file system. Files are exchanged using FTP protocol where host runs FTP service. This component consists of a convenience GUI which shows the progress of the files downloaded or uploaded. Client can get the listing of files on host system using this component. This component supports DBCS.
File Parser
This architectural mechanism provides a uniform approach for parsing of ASCII flat files. It supports position based and delimiter based file parsing. It returns the parsed file as a domain object thus freeing developer from file IO operations. Provision for returning domain objects after each record is parsed or in batch of records is provided so as to maximize memory utilisation as per the application need. It supports two models for parsing viz push and pull. Push model parse pre-configured number of records and send to the client as domain object. Pull model waits for client to request to parse the file sequentially in batches. Client receives an handle to lazy fetch which can be iterated through to generate next batch of records.
Bootstrap
This architectural component assist in initializing required services or components in application server before any client request can be serviced. It also helps in improving performance by ensuring globally required services are initialized and available when required rather than loading them at the time of request. In the channel tier, where there is a web container, a bootstrap Servlet is used. In the application server, which is not expected to host a web-container, this component uses the custom API provided by application server. Hence this component is coupled with application server and is currently available for use in IBM Websphere application server for the application tier.
Data Access Service
This architectural mechanism allows access to the persistent store. It is wrapper on Hibernate ORM that provides XML based mapping of objects to relational mapping. It uses IOC (inversion of control) to keep the connection handles encapsulated from a developer and internally uses a reference counting mechanism to finally close database connection. It throws named exceptions to flag application developers of exceptions that can be handled like no data found.
Batch-Shared OLTP
The framework includes a high performing batch framework. The batch framework will provide application developers a platform to assemble business components to be used in a batch mode. The batch framework provides abstract classes for batch application development. The batch framework uses JMS to stream batch jobs. The batch framework does not use custom threads, but rather uses JMS as the threading mechanism to achieve parallelism in a batch job. A batch job can be distributed across not just processes (JVMs) but across servers (or machines). This provides a lot of flexibility in distributing a job. A batch job can therefore be run on the same server as the OLTP or can be run on a different server. It is also possible to introduce new servers for just batch processing, thereby improving the scalability of the batch framework.
The framework provides an abstract batch data class, which can be extended to set the data for the batch process. The developer therefore needs to extend the class for the batch data. Once the data set has been coded for a particular batch process, then the application developer will need to map the batch data set with the input for the process component that needs to be used for the batch process. To actually execute the batch process, the application developer will need to register the batch process using the batch processing administration GUI provided.
PL/SQL Batch Process
The batch framework also provides a PL/SQL version of the batch framework. The PL/SQL version does not share the OLTP process components or the business common services, but provides a simple high performing batch framework in PL/SQL. PL/SQL offers a “near data processing” batch framework. This framework will provide a high batch throughput on a lower system configuration due to the inherent benefits of processing near the data. This framework will need source code duplication and will increase the maintenance effort of the application. Though this will increase the maintenance effort, this framework cannot be written off as it provides a very high batch throughput. For extremely time critical batch processing, this framework may need to be used. The actual usage of the same will depend on the specific requirements for the application.
Framework
1) Channel Tier
This tier provides various protocol services for communication with Presentation. Converts different message formats to internal standard formats, check validity, and supports posting to hosts that provides actual business services. Features of the channel tier are as below:• Handles multiple request protocols • Comprehensive connectivity to a large variety of systems• Uses Asynchronous IO for TCP/IP • Configurable audit logging with pre and post formatted inputs and outputs• Plug-in support for validations• Re-use validations across transactions• Push data to a client via TCP/IP for long running transactions.
2) Biz Tier
Biz tier comprises of Service Orchestrator, Service Provider and Data abstraction components. Message router in channel tier forward the message to Service orchestrator.
a. Service Orchestrator
This sub component deals with invocation of appropriate service provider for the transaction being sent by message router. It comprises of message listener, transaction coordinator, service command, and process orchestrator.Message Listener is implemented as a message driven bean and provides mechanism for receiving transaction from message router in channel tier. Process orchestrator manages the invocation of one or more than one service commands to execute transaction. Services are invoked synchronously. Process orchestrator caches the work flow information from the repository.Service command converts XML message to the DTO java object as required by service provider which executes the transaction. Service command then invokes service provider using the DTO java object. Following figure shows the flow of transaction within Service orchestrator.
b. Service Provider
This component comprises of process component, EIS wrapper, referential component or domain component. Service provider manages the business processes for the transaction. Service provider communicates with the back end systems that provides the business functionality. Data required by host system is provided by service provider by formatting or generating data from the available data with transaction. Data is retrieved from database using referential component. EIS wrapper acts as a proxy for allowing back end services to be invoked by service provider.
c. System Integration Mechanisms
Component in the service provider communicate with multiple host system via system interface. System interface allows for a standard mechanism for clients to connect to host systems. The system interface consists of a basic interface which is used by clients to communicate with different back-end systems. An interface to a specific back-end system can be obtained via a System interface factory. The system interface factory will create an instance of the appropriate back-end system connector and return the interface for the same. The system interface handles this posting of the reversal, which is completely independent of any application developer intervention. In case the reversal transaction so posted fails, then the transaction is marked as pending reversal in a local log. The log is a database table. When a user initiates another transaction, the reversal transaction is attempted again. This auto reversal function assumes that the host system will return a success for a reversal transaction for which the original transaction does not exist. The auto reversal function will not handle any failures for the reversals sent.
3) J2EE Fundamental Facility
Fundamental facility provides sets of architectural services and architectural classes that can be used for building an application or framework.
Friday 11 January 2008
What level of education is required to understand my blog?

How do they evaluate my blog?I tried to my other blog (written in Korean, but most of contents are open source framework including "Hibernate", "Spring" and other UML and Software architecture artifact) but they evaluate as "high school" (http://blog.naver.com/tooth2)I cannot understand what their criteria is...is it English only?
Thursday 10 January 2008
PAN technology overview
There are several WPAN technologies available; Bluetooth, UWB(Ultra-wide band), and Zigbee.
Bluetooth is nowadays well-known technology.
UWB technology is one of the wireless transmission technology, it can deliver digital data with lower power, more data using wide-spread spectrum in short range. Zigbee is also alternative , it has low complexity for design, low cost, the price is rather cheaper than Bluetooth low power consumption. However its data rate is low , maximum 250kbps,
RFID + WSN Application
Since the US government invested 19$ budget in 2004, several projects have been researched by military service and research institute.
WSN will be used in DoD, health Care, transportation, Industrial Automation, Retail Industry, manufacturing, retail/supply chain, environment , disaster prevention and home network as well.
DoD
If mote can be spread out in enemy's area using remote-controlled spy plane, the mote can make communication network and activate the sensors then it can detect vehicle and its route. There are many research project which are sponsored by military, Vanderbuilt college has researched about ‘Shooter Localization’ project for military purpose and Ohio Sate university has researched about ‘Line in the Sand’ project to figure out enemy’s movement based on vibration sensors and UCLA has developed ‘Power Aware Distributed Systems’ based on vibration and actuator sensors in enemy’s area.
Environment
- Using temperature, humidity, heat, location, vibration sensors, application can detect and control environment in real time and prevent and efficient response when the fire or collapse is occurred.
Disaster Prevention
- Application can decide and notify disaster based on sensing data analysis
Health care
- Application can detect and analyze patients health from bio sensors which can collect pulse, temperature and blood pressure of patient. Through this application, doctors can monitor, diagnose and prescribe the patient in distant when emergency occurs.
If temperature sensor and humidity sensors are attached to blood or anti-cancer medicines, this application can provide right temperature and humidity and raise down blood disposal ratio.
Transportation
- Using vibration, actuator, application can detect crash or traffic and control traffic congestion efficiently in real time.
Retail/Supply Chain
If WSN technology is combined with RFID, then RFID/WSN can be applied retail/supply chain management area very efficiently. RFID will be used in Identification/Access &Tracking, . sensor network can collect, analyze, transmit to monitor & control.
These applications will be commercialized soon according to sensor node manufacturing company such as SAIC (Science Application International Co.) , Dust Networks , Sensicast System
Smart Dust
SmartDust was designed in very small Silicon Mote and integrated with SoC and solar-cell technology in early days.
One component of the sensor node is low-power CPU, this component has been developed by Intel, ARM, and Motorola. Intel developed motes which use micro processor based on ARM 32bit CPU , as following image shows Intel Mote . It has 64KB RAM, 512 KB memory and 12MHz CPU clock. RF Module is based on 2.4GHz Blue tooth which is developed by Zeevo, and its transmit ration is up to maximum 720kbps.
However, the sensor node technology has still outstanding issues such as sensor size , battery life cycle, cost for installation and data accuracy. To solve these issues many research and development project is still going on. By the Dust technologies, current sensor mote size is as small as 1cent, however, it can be recognized by eye, so it can easily exposed to enemy or general human beings who may regard it as “dust” and throw it away.
Second, limitation of battery life cycle can be an obstacle for the deployment. To extend battery’s life cycle there are several approaches has been researched and developed. In initial stage, it is proposed instead of battery, that solar cell is used. However, solar cell cannot minimized mote size and not efficient in energy transformation. Since then, instead on solar cell, acoustic noise and kinetic energy by vibration between the motes are replaced.
l Solar cell
l Energy source from human body (Temperature)
l Source from building(heat)
l Kinetic Energy (by Vibration, by Motion
l Acoustic Noise
Nowadays, other approach for better life cycle is researched by communication engineering area, which is to optimize sensor network To minimize battery exchange cost, there are several efficient communication routing protocol is proposed for example, SMedia Access Control by prof. Wei Ye.
Third, sensor mote’s price is not cheap. Recently, MEMS technology has dramatically led to the development of ultra small in size, low-power, low-cost sensor devices. However, cost is shrink down from 50$/mote to 1$/mote. Still, it will cost huge amount of money to apply and create sensor network in real world.
RFID application use case model + domain model
1) Supply Tracker (search inventory, display inventory, order supplies, update inventory) - primarily used by an individual playing the role of Purchaser
2) People Tracker (admit patient, register visitor, discharge patient, register staff, query person location, monitor visitors, monitor ward) - primarily used by Nurses, Administrative Staff and Security Personnel
Through this project approach can be summarized as following :
1) Supply Tracker Application
- Unauthorized visitor access (e.g. risk of drug theft or infant abduction)
- More effective inventory management
- More effective shared use of high-demand capital equipment (e.g. sonogram machines)
Domain Model
In this problem context, key concerns are RFID tag , People Registration /Asset Registration and Location Event. The others are duplicated information from HR, e-Records and e-Logistics system which is originally managed patient’s medical information, employee’s detail information and asset’s information. By applying “separation of concerns” concept, key abstraction can shows this domain characteristics concisely, however, with other entity can describe well enough to understand this domain as well. Key abstraction (yellow) will be designed first in design stage and others will be designed later and be consistent with existing environment.

E-records is the master domain of patient’s medical information. HR is the master domain of employee’s information such as department, special occupation, and position. E-Logistics is the master domain of asset’s information such as asset category (disposable supplies, expensive equipment, etc) and earned date , earned price, and etc. These entity should be consistent with original master entity in HR, e-Records, and e-Logistics. To meet consistency, in design stage, these entities should be designed to meet their original domain’s design specification such as database schema, interface specification and etc.
RFID application proposal for Hospital
This proposal contains:
(2) Recommendation of the ten best applications of RFID for a hospital using the four criteria
(3) Recommendation of the ten solution deployment strategy for the next five years
(4) Estimation of deployment costs for recommended solution including RFID devices and support systems.
 Specifically out of scope are systems and the networks architecture on which they run and the management of these systems and operation systems. However it is expected that the cost estimation of recommended solution will need assumption of generic architecture which can be applied to the implementation plan of these systems.
Specifically out of scope are systems and the networks architecture on which they run and the management of these systems and operation systems. However it is expected that the cost estimation of recommended solution will need assumption of generic architecture which can be applied to the implementation plan of these systems.When the client wants to use RFID throughout the hospital for many different purposes, including patient identification, billing, surgical safety, personnel location and, of course, drug tracking. The client understands that it will be able to control some of the RFID systems, such as patient identification, but for others it must remain compatible with RFID tags coming from outside entities, such as drug companies. The client also sees RFID as the beginning of "ubiquitous computing" in the medical field.
The client understands ubiquitous computing to mean that in the future numerous computers and chips will be embedded in the walls of rooms, in surgical instruments, laboratory apparatus, patient blood sample containers, employees badges, patient wristbands - essentially all over the hospital. These devices can interconnect through wireless technology to form a vast network of computers and sensors that will allow automation of many functions now performed manually, such as capture of billing information. It expects that this technology will be able to improve the efficiency and safety of health care delivery.
The question that the client asked which set of technologies should be used, how can it be sure to be compatible with outside products having RFIDs, and what future applications can be developed to
The client is looking for a far-ranging, creative implementation of RFID-based ubiquitous computing in its hospitals. It will also need to understand the cost of various alternatives.
Summary of Result
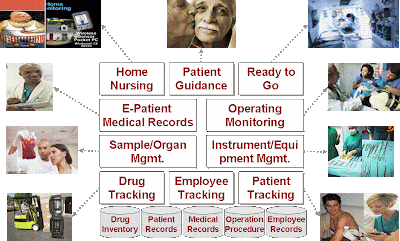
1. Ready to Go, will provide emergency check before ambulance leaving
2. Operation Monitoring will improve patient safety by check and monitoring before/while operation
3. Surgical Instrument/Equipment management system will provide the status of surgical instrument – for e.g. Sterilization/contamination/infection and etc.
4. Patient Tracking will provide patient we will look through in next slides and protect infant stolen by real-time notification as well.
6. Drug Tracking is the FDA compliance Application and also provide drug inventory as well.
7. Sample/Organ Management will provide Identification and speed up test center’s billing process as well.
8. e-Patient Medical Record will provide right Medication and Speed up diagnosis process as well 9. Home Nursing System will provide 24hours home care service for special patient like diabetic patient etc.
10.Patient Guidance system will protect elderly or blind people getting lost in the hospital and provide navigation information by headset.
RFID technology overview
 Ubiquitous, as defined by Merriam-Webster Dictionary, means “existing or being everywhere at the same time”. Based on this, ubiquitous computing is the computing environment that is everywhere; it is in the environment surrounding us and becomes part of our life, and as the technology is almost transparent to us, it does not become a distraction. As RFID provides a way of making “things communicate with other things” (understanding things as machines, products, etc.), people can just live their lives and let the technology work by itself.
Ubiquitous, as defined by Merriam-Webster Dictionary, means “existing or being everywhere at the same time”. Based on this, ubiquitous computing is the computing environment that is everywhere; it is in the environment surrounding us and becomes part of our life, and as the technology is almost transparent to us, it does not become a distraction. As RFID provides a way of making “things communicate with other things” (understanding things as machines, products, etc.), people can just live their lives and let the technology work by itself. - Freqeuncy issue
The 3 main frequencies used for RFID purposes are: HF(13.56 MHz), UHF(860 MHz – 930 MHz), and Ultra UHF( 2.45 GHz). The first one fits in the category of High Frequency (HF) and the other two in the Ultra High Frequency category (UHF). Generally speaking, by using a higher frequency you can improve a tag reader's ability to read many co-located tags because of the higher data transfer rate, reducing the chance of collision. [07/want04] It is also possible to read tags at bigger distances (up to 100 meters with active RFIDs) while increasing the frequency.
HF is cheaper than UHF technology and HF can be recommended for most of the applications, especially when a large number of tags/readers are required. If the application is going to be used within the hospital, HF can be recommended for cost reasons as well. For drug tracking UHF can be recommened , because the need of interoperability with other health centers and the FDA.
If a further range of operation is needed or tag size is not important, probably 900MHz frequency can be recommended. If more functions are needed, 2.45GHz frequency can be recommended because it is easier to integrate with sensors and has more functions, but cannot be used inside operation rooms or near people with pacemakers.
When mobility is a must, portable readers should be used. These machines have their own operating system and usually have the ability to send data to a central computer through a wireless connection. Otherwise, fixed readers should be used (portable readers cost 2-5 times of a fixed one).
HF has a lot of advantages in size and antenna design, but has a very short operation range. On the contrary, 900MHz offers a very long range and a great tolerance to interference (medium to water/metal) but a bigger tag size and more complex antenna design. The 2.45GHz also has very small size tag, but it is not so tolerant to interference as 900MHz and has a shorter range, although the antenna design is a little bit easier. Both HF and 900MHz should be able to work with metal/water and avoid most of interference, and their bigger differences are in size and range.
- Data Standardization issue
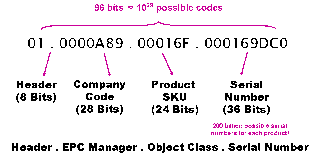
The EPCglobal standard defines the EPC code within its Architecture Framework. Other important standards are the ONS (to locate authoritative metadata and services) and the EPCIS (provides a service interface to access information from the central DB or repository).
The EPC is defined by EPCglobal as a code to identify the manufacturer, the type and unique id of a given product. It uses 96 bits, where 38 are for identifying its serial number (see table below). That means it can have 2^38 (270+ billion) unique serial numbers for each product and company. EPCglobal Tag Data Standards Version 1.3 defines all these details.
- RFID tag with Material issue
- Privacy and Security Issue
-Smart tags
-PKI capable tags
-Anonymous-ID scheme
-Tag with lightweight circuits: i.e. hash function
- Algebraic Eraser
Book: Through the Looking-Glass by Lewis Carroll
Through the Looking-Glass (1871) is a work of children's literature by Lewis Carroll (Charles Lutwidge Dodgson), generally categorized as literary nonsense. It is the sequel to Alice's Adventures in Wonderland (1865). Although it makes no reference to the events in the earlier book, the themes and settings of Through the Looking-Glass make it a kind of mirror image of Wonderland: the first book begins outdoors, in the warm month of May, on Alice's birthday (May 4),[1] uses frequent changes in size as a plot device, and draws on the imagery of playing cards; the second opens indoors on a snowy, wintry night exactly six months later, on November 4 (the day before Guy Fawkes Night),[2] uses frequent changes in time and spatial directions as a plot device, and draws on the imagery of chess. In it, there are many mirror themes, including opposites, time running backwards, and so on.
This book was reported that many software architect and software engineering people got insight from it.



